Microsoft’s Digital Crimes Unit (DCU) has seized 240 fraudulent web sites related to an Egypt-based cybercrime facilitator. Abanoub Nady (identified on-line as “MRxC0DER”) developed and offered “do it your self” phish kits and fraudulently used the model title “ONNX” to promote these companies. Quite a few cybercriminal and on-line menace actors bought these kits and used them in widespread phishing campaigns to bypass extra safety measures and break into Microsoft buyer accounts. Whereas all sectors are in danger, the monetary companies trade has been closely focused given the delicate information and transactions they deal with. In these situations, a profitable phish can have devastating real-world penalties for the victims. It may end up in the lack of important quantities of cash, together with life financial savings, which, as soon as stolen, might be very troublesome to recuperate.
Phishing emails originating from these “do it your self” kits make up a good portion of the tens to tons of of thousands and thousands of phishing messages noticed by Microsoft every month. The fraudulent ONNX operations are a part of the broader “Phishing-as-a-Service” (PhaaS) trade and as famous on this yr’s Microsoft Digital Protection Report, the operation was among the many high 5 phish equipment suppliers by e mail quantity within the first half of 2024. Very like how e-commerce companies promote merchandise, Abanoub Nady and his associates marketed and offered their illicit choices via branded storefronts, together with the fraudulent “ONNX Retailer.” By focusing on this distinguished service, DCU is disrupting the illicit cybercriminal provide chain, thereby defending prospects from a wide range of downstream threats, together with monetary fraud, information theft, and ransomware.
Concentrating on rising cyber threats to guard customers on-line
The fraudulent ONNX operation illustrates the advancing sophistication of on-line threats, together with refined “adversary-in-the-middle” (AiTM) phishing strategies. As organizations strengthen their cybersecurity measures, cybercriminals are evolving their techniques to evade them. AiTM phishing assaults – the place attackers secretly inject themselves in community communications to steal credentials and cookies used to authenticate customers’ id – have change into extremely favored, if not the “go-to” technique utilized by malicious actors to bypass the extra protections of Multifactor Authentication (MFA) defenses. As famous on this yr’s Microsoft Digital Protection Report, Microsoft has noticed a 146% rise in these AiTM assaults alone.
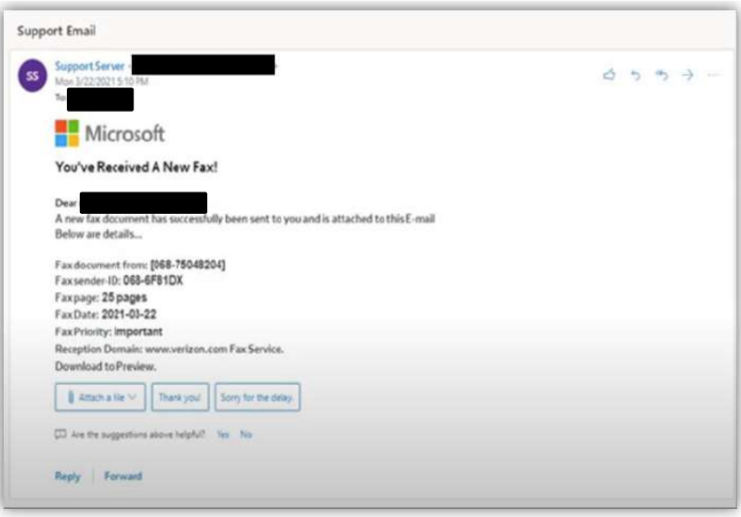
FINRA, the not-for-profit self-regulatory group that oversees U.S. broker-dealers, lately issued a public Cyber Alert, warning of a spike in AiTM assaults in opposition to members fueled by the fraudulent ONNX operation. On this warning, FINRA highlighted new strategies employed by cybercriminals together with QR code phishing (quishing) to bypass cybersecurity protections. “Quishing” makes use of embedded QR codes that, if scanned, direct on-line customers to malicious impersonation domains — sometimes a faux sign-in web page the place customers are prompted to enter credentials. Starting round September 2023, Microsoft analysts noticed a major enhance in phishing makes an attempt utilizing QR codes (to almost one quarter of all e mail phishes). These assaults current a singular problem for cybersecurity suppliers as they seem as an unreadable picture.
Sending a powerful message to cybercriminals
This motion builds on the DCU’s technique of disrupting the broader cybercriminal ecosystem and focusing on the instruments cybercriminals use to launch their assaults. Our purpose in all instances is to guard prospects by severing unhealthy actors from the infrastructure required to function and to discourage future cybercriminal conduct by considerably elevating the boundaries of entry and the price of doing enterprise.
We’re joined by co-plaintiff LF (Linux Basis) Initiatives, LLC, the trademark proprietor of the particular registered “ONNX” title and emblem. “ONNX” or Open Neural Community Change is an open commonplace format and open supply runtime for representing machine studying fashions, enabling interoperability between completely different {hardware}, frameworks, and instruments for simpler deployment and scalability.
Collectively, we’re taking affirmative motion to guard on-line customers globally relatively than standing idly by whereas malicious actors illegally use our names and logos to reinforce the perceived legitimacy of their assaults. As well as, and as DCU has in previous actions the place we independently determine an actor, now we have chosen to publicly title a defendant – Abanoub Nady, who led the fraudulent ONNX operation – to function an extra deterrent for cybercriminals and malicious actors on-line.
Concerning the fraudulent ONNX felony operation
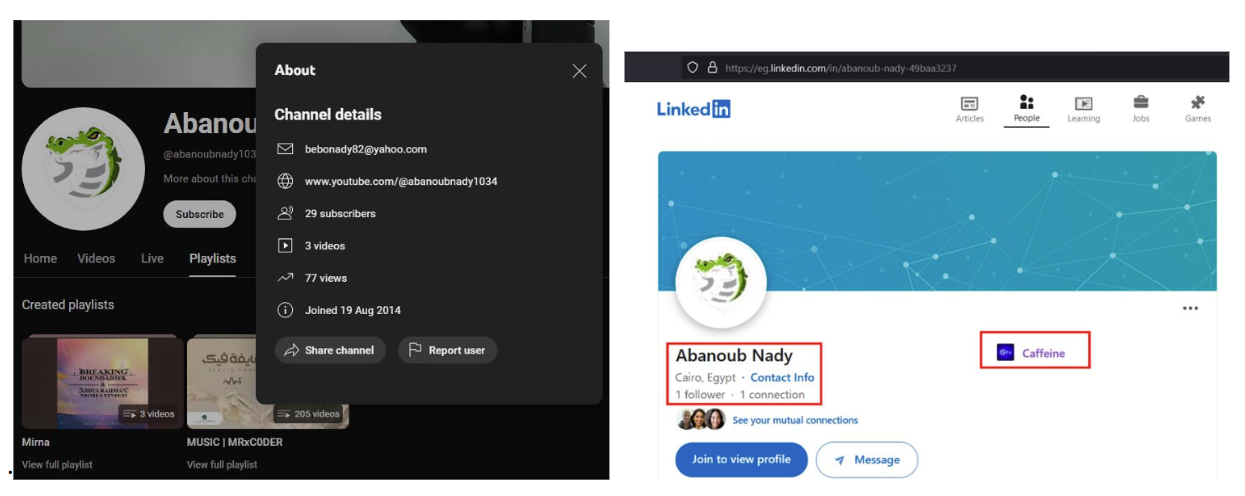
Many cybersecurity corporations have regarded into and revealed studies on the fraudulent ONNX operation, together with DarkAtlas which Abanoub Nady earlier this yr and EclecticIQ, which detailing how fraudulent ONNX operations have been getting used to focus on monetary establishments. Microsoft has tracked exercise tied to Abanoub Nady’s operation way back to 2017. Nady fraudulently used the ONNX model, however he additionally used different names in his operation, together with “Caffeine” and extra lately DCU noticed Nady operating the “FUHRER” operation. The phish kits are designed to ship emails at scale, particularly for coordinated phishing campaigns. As an illustration, the fraudulent ONNX operation presents a subscription mannequin, providing Primary, Skilled, and Enterprise subscriptions, every for various tiers of entry and assist. Enterprise customers can even buy the add-on function of “Limitless VIP Help,” which is basically ongoing technical assist that gives step-by-step directions on learn how to efficiently use the phishing kits to commit cybercrime.

The phish kits are promoted, offered and configured virtually completely via Telegram, as proven within the instance under, that are paired with “learn how to” movies on social media platforms that present steering on the acquisition and implementation of those phishing kits.
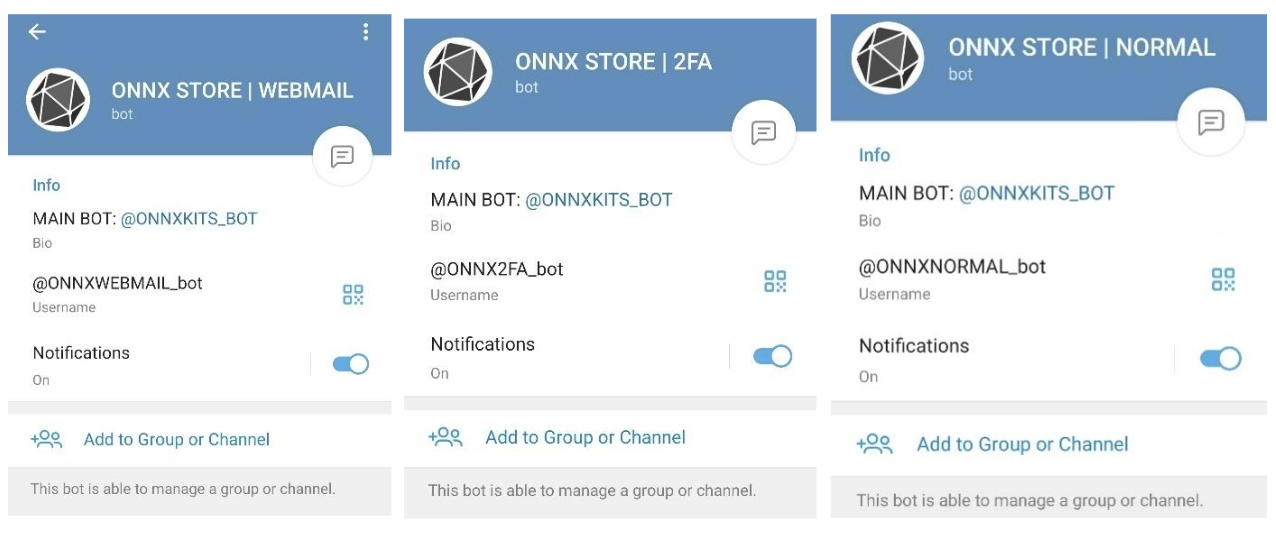
As soon as a equipment is bought, cybercriminal prospects can conduct their very own phishing assaults utilizing the templates offered and the fraudulent ONNX technical infrastructure. They will use domains they buy elsewhere and hook up with the fraudulent ONNX technical infrastructure, enabling their phishing operations to develop and scale.
By way of a civil court docket order unsealed at this time within the Japanese District of Virginia, this motion redirects the malicious technical infrastructure to Microsoft, severing entry of menace actors, together with the fraudulent ONNX operation and its cybercrime prospects, and completely stopping the usage of these domains in phishing assaults sooner or later.
Persevering with our combat in opposition to the instruments cybercriminals use of their assaults
As we’ve mentioned earlier than, no disruption is full in a single motion. Successfully combatting cybercrime requires persistence and ongoing vigilance to disrupt new malicious infrastructure. Whereas at this time’s authorized motion will considerably hamper the fraudulent ONNX’s operations, different suppliers will fill the void, and we count on menace actors will adapt their strategies in response. Nevertheless, taking motion sends a powerful message to those that select to copy our companies to hurt customers on-line: we’ll proactively pursue treatments to guard our companies and our prospects and are repeatedly bettering our technical and authorized methods to have better influence.
Moreover, as cybercriminals proceed to evolve their strategies, it’s essential for organizations and people to remain knowledgeable and vigilant. By understanding the techniques employed by cybercriminals and implementing strong safety measures, we are able to collectively work in direction of a safer digital setting. Continued collaboration, just like the partnership with LF Initiatives, stays important if we need to meaningfully dent the cyber menace panorama.
Microsoft’s DCU will continue to search for artistic methods to guard folks on-line and work with others throughout private and non-private sectors globally to meaningfully disrupt and deter cybercrime.
Nov. 11, 2024, 11:48a PT: Up to date to incorporate extra analysis on the fraudulent ONNX operations by different cybersecurity corporations.

